The Emergence of the RuskiNet and Moroc
A New Chapter in Hacktivism - By CybSecTools.com
In the ever-evolving landscape of cyber warfare, alliances between hacktivist groups have become increasingly prominent. One of the latest and most notable developments is the reported collaboration between RuskiNet and MoroccanCyberForces, two hacktivist organizations that have joined forces to target nations such as the USA, Canada, Turkey, Israel, the UK, and India.
This alliance underscores a growing trend of cyber collectives aligning their capabilities and motivations to amplify their impact on global geopolitical events.
Background of the Groups
Although public information about RuskiNet is limited, its name suggests an affiliation with Russian cyber operations. Russia has a well-documented history of using cyber strategies to advance geopolitical interests. The broader ecosystem includes state-sponsored hackers, patriotic cyber actors, and organized cybercriminals, forming a layered and complex network of cyber capabilities.
MoroccanCyberForces, in contrast, appears to reflect Morocco’s rising investment in cyber warfare. The country has taken visible steps to develop its electronic warfare competencies. Notably, the Moroccan Royal Armed Forces have collaborated with the U.S. Army Cyber Command in joint electronic warfare training exercises, such as African Lion 2024, showcasing Morocco’s interest in international cyber defense partnerships.
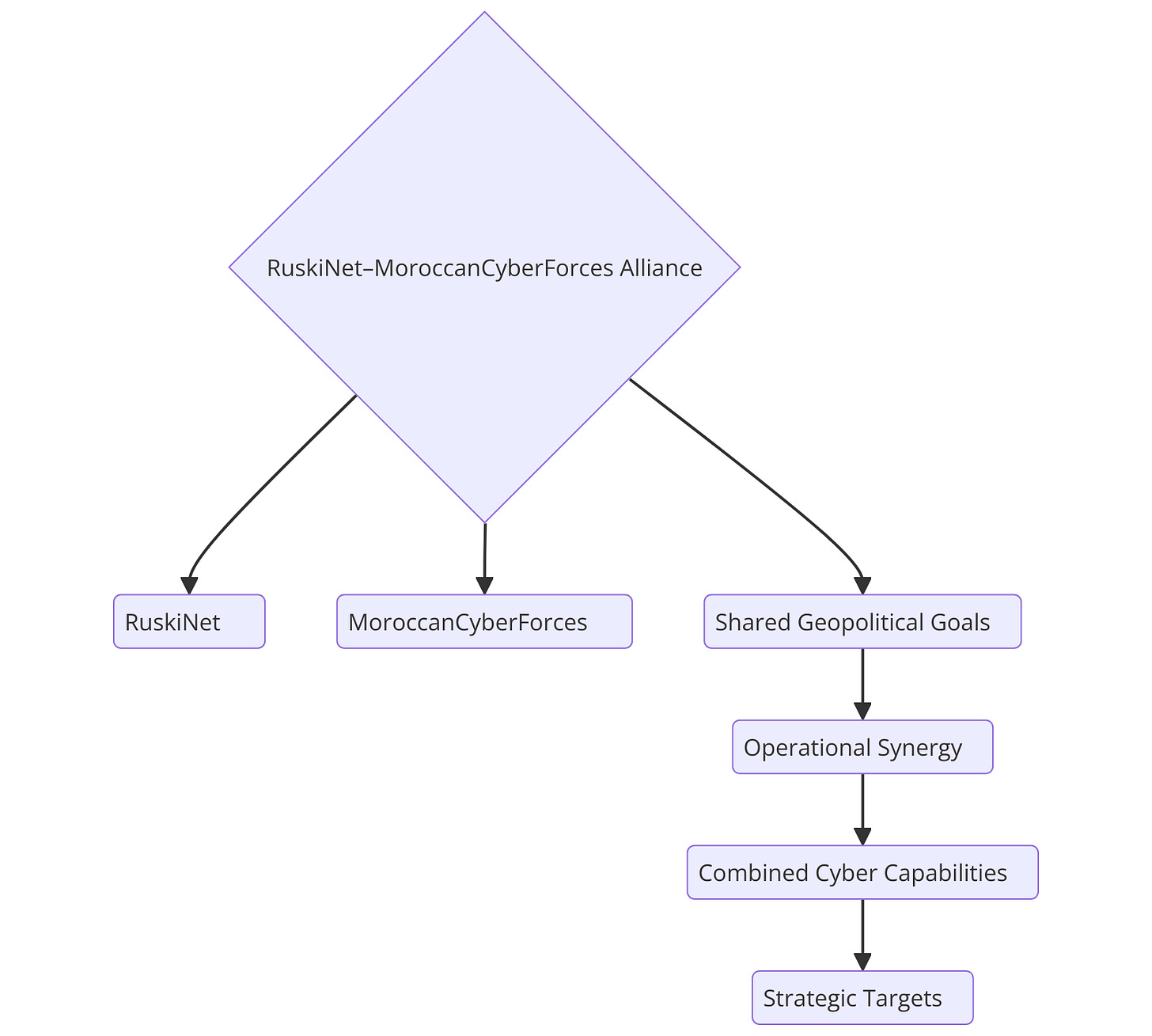
Motivations Behind the Alliance
The emergence of a RuskiNet–MoroccanCyberForces collaboration can likely be attributed to:
Shared geopolitical goals
A desire to enhance operational effectiveness
Access to complementary resources and knowledge
These kinds of alliances are not new. The cyber domain has seen multiple examples where ideologically or politically aligned groups unite to extend their capabilities, whether to deliver more sophisticated attacks or to increase psychological impact through high-profile targets.
Targeted Nations and Strategic Implications
The alliance has reportedly focused on six major geopolitical players:
🇺🇸 United States
🇨🇦 Canada
🇬🇧 United Kingdom
🇮🇱 Israel
🇮🇳 India
🇹🇷 Turkey
Attacks on these nations can have serious implications, such as:
Disruption of critical infrastructure
Theft of classified or sensitive data
Influence operations and public disinformation
Geopolitical escalation through digital proxies
For example, the Moroccan Black Cyber Army, which is believed to have ties to MoroccanCyberForces, has claimed attacks against Israeli infrastructure in the past. This further suggests that ideological and political motivations play a central role in these operations.
Visualizing the Alliance and Its Targets
Below are two diagrams created to better understand this alliance and its geopolitical scope:
1. Structure and Motivation of the Alliance
Photo: Alliance Structure Flowchart.
2. Target Countries and Strategic Impacts
Geopolitical Mindmap of Targeted Nations
Broader Context of Hacktivist Alliances
This alliance is not an isolated event—it reflects a significant shift in how hacktivist groups operate:
Moving from solo or localized actions to multi-national collaborations
Sharing infrastructure, intelligence, and code
Increasing the frequency, complexity, and visibility of their attacks
Such developments make the cyber threat landscape more dynamic and unpredictable. They also blur the lines between hacktivism, cybercrime, and cyber warfare.
Conclusion
The reported collaboration between RuskiNet and MoroccanCyberForces exemplifies the shifting dynamics of modern cyber threats. As these alliances become more coordinated and politically charged, understanding their motivations, tactics, and likely targets is essential for developing effective cyber defense strategies.
This case also highlights the urgent need for:
International cooperation in cybersecurity
Strengthened cyber resilience for national infrastructures
Continued monitoring of cyber threat actors and their evolving alliances
CybSecTools.com
Security isn’t optional. Knowledge isn’t either.